
Advanced Vulnerability Detection:
Use of Deep Learning algorithms enables
a drastic reduction in false positives.

Automated and Simplified:
Hassle-free automation of smart contract
audits in three simple steps.


Quick and Efficient:
Accurate and reliable results with a
response time of less than 2 seconds.
Reconeyes: AI-Driven Security for Smart Contracts
Getting Started
- Reconeyes presents a scalable framework for automated smart contract auditing, specifically designed for EVM-compatible smart contracts. It promises unparalleled accuracy and reliability. By integrating advanced machine learning algorithms with comprehensive static analysis, Reconeyes significantly reduces false positives, enhancing accuracy.
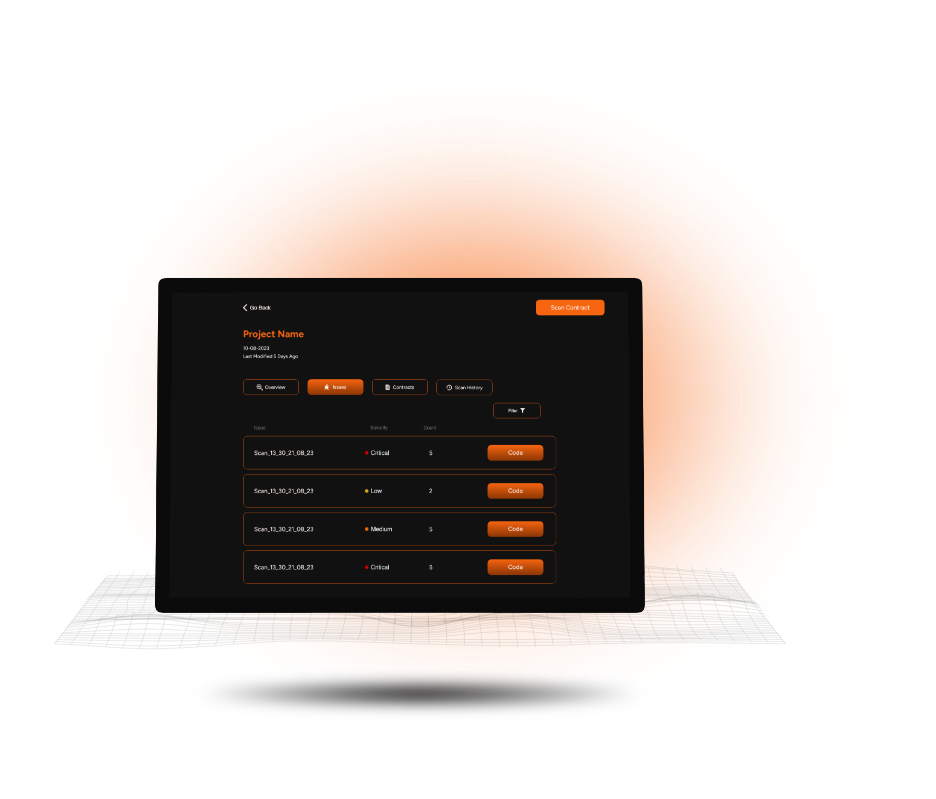
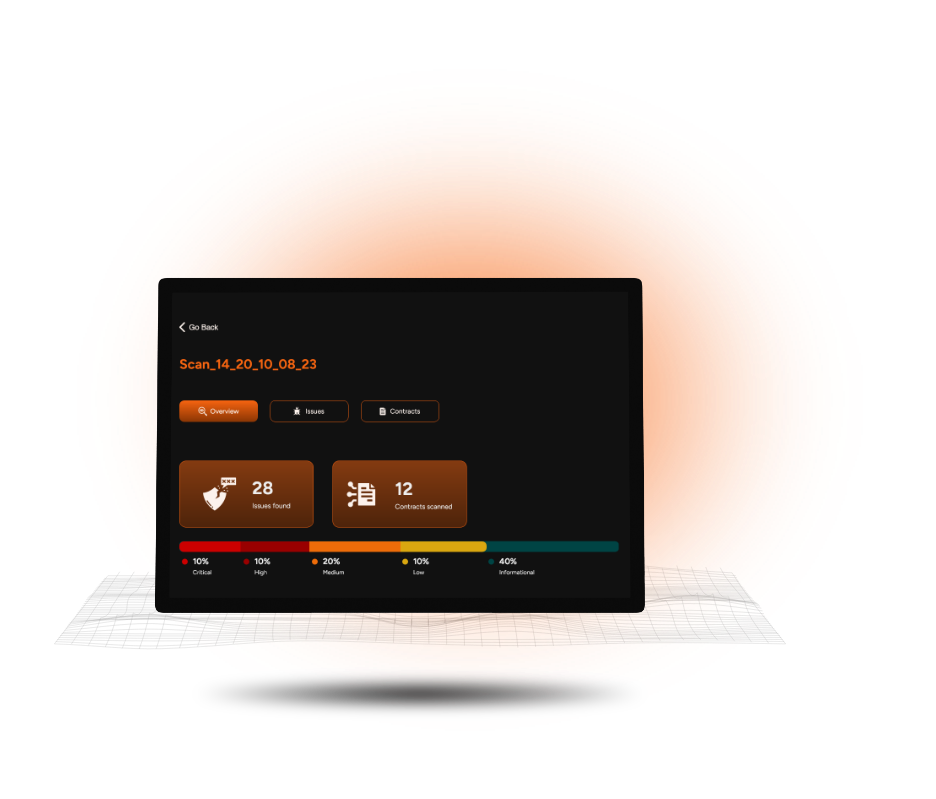
- Scanning for over 80+ known Solidity vulnerabilities, including those in the SWC registry, and supporting the latest Solidity versions, Reconeyes ensures you have the most accurate and up-to-date analysis. Its user-friendly interface streamlines the audit process, making it faster and easier to secure smart contracts against potential threats.
- With Reconeyes, you can ensure your smart contracts are robust, secure, and ready for deployment in the dynamic blockchain landscape.

Upload your smart contracts from a GitHub repository or your device.
Reconeyes analyzes your code, identifying and locating potential vulnerabilities.
Immediate results with actionable insights, without the clutter of false positives.
Frequently Asked Questions
By learning from vast datasets of smart contracts, our ML models can predict and identify vulnerabilities with far greater accuracy than traditional methods like static analysis. In the first version, Reconeyes detects 30 known vulnerabilities with ~99% accuracy and largely reduces the occurrence of false positives in traditional static analysis methodology.
Reconeyes is designed to complement manual auditing by enhancing efficiency and accuracy through its AI abilities. While it significantly reduces the need for manual checks by automating vulnerability detection, a comprehensive security approach may still benefit from the insights of manual audits. Combining Reconeyes' automated capabilities with expert manual review ensures the highest level of security for smart contracts.
Reconeyes integrates seamlessly into your development and auditing workflows. It can be used at various stages, from initial development to final audit, providing continuous security monitoring. By incorporating Reconeyes early and regularly in your CI/CD pipeline, you can detect and address vulnerabilities throughout the development lifecycle, ensuring robust smart contract security before deployment.
Getting started with Reconeyes is easy. Simply sign up on our website, upload your smart contract via GitHub or your device, and receive detailed security insights in minutes. You can check out the detailed User Guide here.
Reconeyes is capable of detecting vulnerabilities that are syntactical and logically erroneous, without actually executing the smart contract. It detects a wide range of vulnerabilities, including re-entrancy, unauthorized access, conditional inconsistencies, and more. You can find the complete list of attack vectors here.


